This guide provides a conceptual overview of OneSDK integration with basic code examples. The code snippets shown are illustrative and need to be adapted into your specific framework and application architecture.
For complete, working examples:
- See our Framework Integration Guides for Angular, React, Vue.js, Next.js and other frameworks
- Visit our GitHub repository for extensive sample code and reference implementations
- Check out our Hosted Implementation Examples for end-to-end solutions hosted by FrankieOne
Core Modules Overview
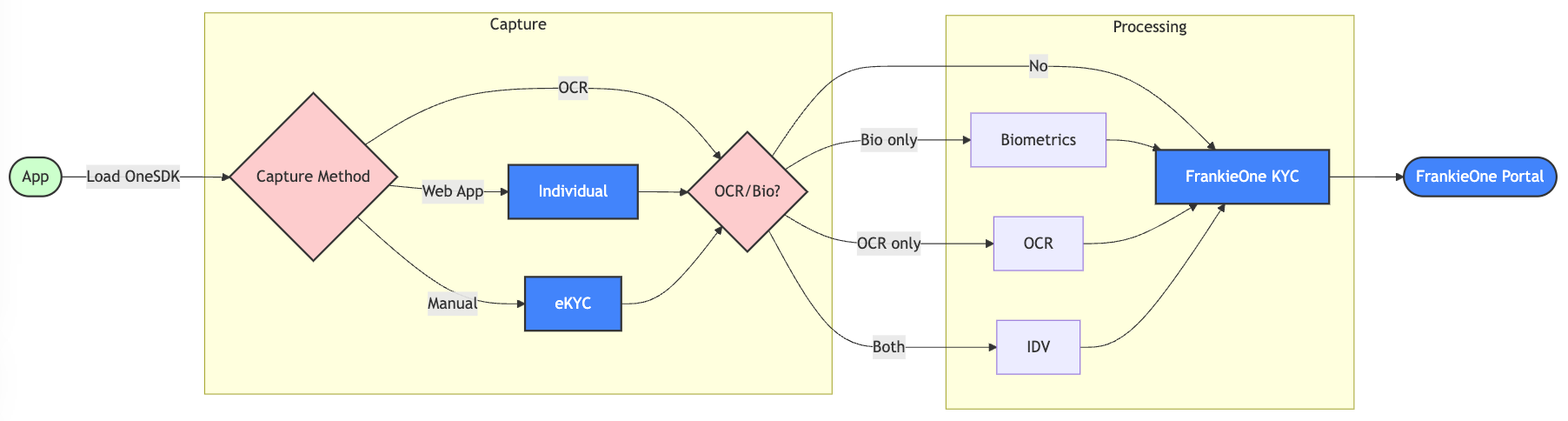
Individual Module
Complete KYC workflow for individual verification, including document handling, address verification, and profile management.
Biometrics Module
Advanced biometric verification capabilities including facial recognition,
liveness detection, and matching.
OCR Module
Intelligent document scanning and data extraction for IDs, passports, and
other verification documents.
IDV Module
Comprehensive identity document verification with support for multiple
document types across jurisdictions.
eKYC Form Module
Customizable electronic Know Your Customer forms with built-in validation and
compliance checks.
Fraud Detection Module
Real-time fraud prevention and detection across multiple risk vectors.
OneSDK Modules Data Capture Flow
Quick Integration Guide
Initialize the SDK
Note: The sample code below is just an example. Never generate tokens on the frontend — doing so can expose your credentials.
Always generate tokens securely on your backend and pass them to your app as needed.
Implementation Best Practices
Error Handling
Error Handling
Module Coordination
Module Coordination
Performance Optimization
Performance Optimization
Initialize modules only when needed and release resources after use. This is especially important for camera-based operations in the Biometrics and OCR modules.
Common Integration Scenarios
- Basic KYC
- Enhanced Verification
Each module can be used independently or as part of a comprehensive
verification flow. Check individual module documentation for detailed
implementation guidelines.
Content Security Policy (CSP) Settings
You may need to adjust your Content Security Policy (CSP) settings to allow vendors’ scripts and resources to load correctly. Below are the additional CSP rules required based on the vendor you are integrating with:- Onfido
- Incode
- Truuth